
15 Sep, 2014
Snowden leak: U.S. Govt tapping expats to help maintain global “supremacy”
From students to academics and businesspeople, American expatriates and citizens are being tapped to provide the U.S. government with information on anything that could help uphold its global supremacy, especially in the sectors of business, science, technology and defence, according to the latest Edward Snowden leak published by journalist Glenn Greenwald on 05 September.
The leak of the Quadrennial Intelligence Community Review (QICR) 2009 makes clear the following:
(+) U.S. national security, geostrategic leadership and supremacy are all seen as being part and parcel of the same package; a threat to one is seen as a threat to the other.
(+) Information is power, and the U.S. government is attempting to vacuum up just about everything that can help it influence policy and safeguard U.S. national security interests.
(+) Preservation of the power of U.S. multinationals is seen as being critical to the power of the U.S. government. Foreign multinationals and emerging countries such as the Brazil, India, China, South Africa and, to some extent, Iran, are seen as potential threats, especially if they begin to work together.
The document has immense importance for the travel & tourism industry because U.S. multinational hotel corporations, credit card giants, Internet companies, bookings and reservation websites, and more, are all dominant players in their respective areas, and hence potential contributors to the U.S. policy agenda.
Mr. Greenwald’s reporting of the original leak, published here, focussed on one aspect of the QICR. But there is a lot more to it than that. The entire QICR can be downloaded in full from Mr. Greenwald’s website, The Intercept.
Starting off with the keywords, “If one does not consider the long-range future, one will never cease to be surprised,” the Quadrennial Intelligence Community Review (QICR) is designed to provide a long-term perspective of scenarios that could emerge over 10-20 years. It “complements shorter term assessments, challenges basic assumptions, exposes the potential risks of extrapolating tomorrow’s needs from today’s conditions, and examines missions and capabilities in light of alternative futures,” the report says.
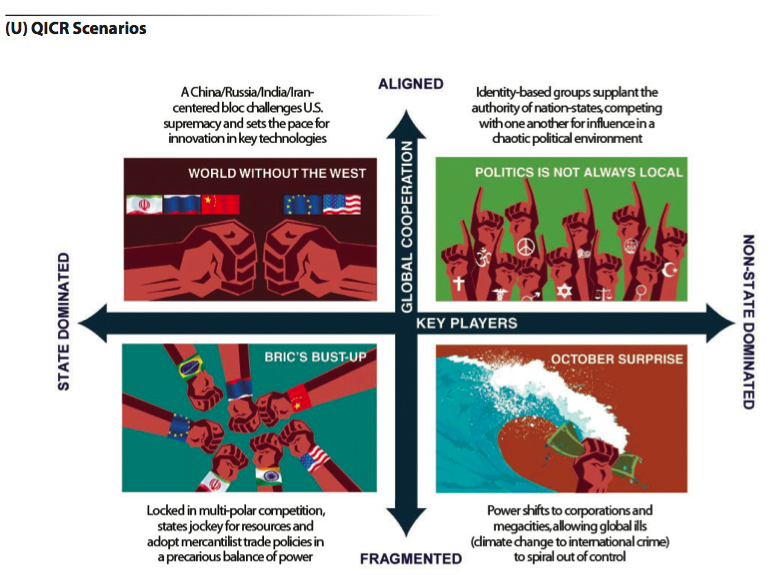
The result of a 10-month effort that involved U.S. departments and agencies, academia, think tanks, and industry, it made three key assumptions about the future landscape for intelligence:
“First, other actors will increase in power and relevance relative to the United States. Second, the information environment will radically transform in scope, complexity, and intensity, with intelligence targets operating seamlessly and simultaneously between the physical and virtual worlds. Third, customers and the IC workforce will be “digital natives” with different operating models and expectations for how to perform and leverage the business of intelligence.”
It identifies three concepts (“safe bets”) that “appear critical to the success of the IC across a wide range of possible futures” and three “Strategic hedges” which are what-if “concepts deemed highly relevant in some possible futures but less relevant in others, which the IC may need to develop as circumstances warrant.”
The QICR cites various efforts that will need to be made to action the policy agenda and “help turn future challenges into opportunities.” These will include covert and clandestine operations, such as setting up front companies; penetrating corporations, markets, foreign central banks, and foreign finance ministries; and more.
It is part of a quadrennial report which means that it was probably updated again in 2013. However, the underlying scenarios are still valid, in which case the proposed action plans to counter the threats are still valid, too. Quotes from the report:
(+) Overtly, the IC (Intelligence Community) would monitor open markets in stocks, commodities, and currencies. To acquire non-public but unprotected data such as proprietary business information, it would use two-way information sharing with trusted and cooperative corporations and foreign governments. Clandestinely, the IC would use human and technical means, including sophisticated tracking software, to access closely held market, financial, and business data, be it inside corporations, foreign governments, or other institutions.
(+) The IC would need the ability to access proprietary sources of information in permissive environments such as foreign universities, industry trade shows, and government conferences. This could include cooperating U.S. students, professors, and researchers reporting bits of non-public information that by themselves are not sensitive, but in aggregate could help the IC make inferences about breakthrough technological innovations. The key challenge would be working closely with the academic and scientific communities (which would include non-U.S. persons), gaining trust, and monitoring potential “threats” while continuing to advance U.S. scientific progress.
(+) The IC would need a concept of Money Mastery to penetrate corporations, markets, foreign central banks, and foreign finance ministries and organizations so that it could gather and analyze proprietary data. The IC also would need to track critical commodities markets in much greater detail as well as the full range of illicit financial markets and economies. This concept would far exceed today’s approach to financial and economic intelligence in scale and scope and would require increasingly sophisticated targeting expertise, even more aggressive HUMINT collection, and processing tools.
(+) The IC would increasingly need to employ a virtual presence to complement its physical presence. That presence would include maintaining a forward position inside unconventional partner and target entities by routinely embedding officers not only in foreign intelligence services, as it does today, but also in cooperative non-state groups. The IC would also routinely employ private citizens as proxies for sensitive analytic and collection tasks. Academics, business people, and others would form an IC-led standing dialogue, participating in collaborative analytic teams when and as their expertise warranted.
(+) Cyber Operations. The IC would sustain close-access collection, frequently by second and third parties, to non-public and/or covert centers of innovation by implanting applications (i.e., bots) that run automated tasks and sensors in software and hardware used by foreign researchers and manufacturers, and by conducting computer-network exploitation of foreign R&D intranets. In select instances, this could also involve development of long-term sources.
In the field of science and technology, the report frets about a potential slipping of U.S. “technological and innovative edge” thus:
“QICR identified two scenarios in 2025 in which the United States’ technological and innovative edge slips — despite our countervailing efforts — and shifts to denied areas. Under one scenario, a bloc of states actively seeking to undermine U.S. geostrategic leadership could deny access to key emerging technologies. Another possibility is that the technological capacity of foreign multinational corporations could outstrip that of U.S. corporations. The IC would be challenged to understand technological innovation outside its traditional competencies (e.g., weapons systems) and in domains where it traditionally has focused less effort (e.g., commercial research and development (R&D). Because technological advancement tends to be exponential rather than linear, either development could put the United States at a growing — and potentially permanent — disadvantage in crucial areas such as energy, nanotechnology, medicine, and information technology.”
In an illustrative example on “technology acquisition by all means,” it describes the modus operandi to counter a prospective threat scenario thus:
“India and Russia are pursuing high-temperature superconductivity, which would yield a significant economic advantage to the first adopter. But four separate streams of intelligence, when put together, yield a new insight — the two countries are working together. Sustained reporting from open and clandestine sources enables a team of experts from the IC, academia, and industry to assess the likelihood – moderate – and impact – high – of a breakthrough by India and Russia. Counterintelligence reporting suggests the two countries are not very interested in U.S. superconductivity efforts, which may indicate they believe they have a secure lead. The IC makes separate clandestine approaches to India and Russia to break up the partnership. It conducts cyber operations against research facilities in the two countries, as well as the intellectual “supply chain” supporting these facilities. Finally, it assesses whether and how its findings would be useful to U.S. industry.”
It also makes a singular but potentially significant reference to a “BRIC’s Bust-Up” thus: “As the United States struggles to maintain its world standing amidst competing and insular blocs, the IC is predominantly focused on economics and commercial science and technology (S&T) missions.”
Says the report, “Four broader implications arise from the QICR 2009. First, the IC will have to manage highly fluid relationships to deal with the dynamism of a more competitive national security environment. Second, it will need to manage a singular operational architecture to deal with the new ways that a greater volume of information will flow. Third, the IC will need to maintain strong information and identity assurance to address the likely erosion in its technological advantage and the new dynamics of the digital medium. Fourth, the IC will need to change the role of the intelligence officer to deal with a dynamic external environment and adapt to new customer needs.”
It says in conclusion, “QICR 2009 highlights the urgency to begin developing new approaches to prepare for an uncertain future. Elements of the National Intelligence Program, foreign intelligence services, state, local, and tribal governments, and industry are encouraged to consider these insights in conducting their own long-term planning efforts. The rigor with which QICR 2009 developed these ideas to mitigate strategic and institutional risk must now be translated into meaningful agenda items for the IC and its partners to carry forward.”
==============
COMMENTARY: AN INTELLIGENCE SCENARIO DOOMED TO FAIL
By Imtiaz Muqbil, Executive Editor.
When Edward Snowden began leaking information about U.S. government intelligence activities to journalist Glenn Greenwald two years ago, he specifically cited them as a violation of the traditionally held values of the U.S., as enshrined in the U.S. Constitution. The latest leak of the QICR proves exactly what he is referring to.
Couched in government gobbledygook, the QICR needs to be read several times in order to be fully understood. But once its key messages are clear, it contains some shocking revelations about how the U.S. government is seeking the unilateral right to act in just about any way it pleases, all within a for-us-or-against-us confrontational framework.
All these efforts are designed to meet the needs of what the QICR refers to as “customers”, which includes various arms of the U.S. government, its multinational corporations and intelligence agencies of like-minded countries. Indeed, the report underscores how the U.S. government will do everything to preserve U.S. power and thwart any efforts to undermine it. This flies in the face of the “freedom and democracy” and “transparency and accountability” it purports to promote. The report also disproves all claims about “conspiracy theories” in relation to U.S. actions, policies and strategies.
From a geopolitical perspective, this my-way-or-the-highway approach becomes a potentially serious global problem, one that is also doomed to fail.
The U.S. is a dominant military power but a fading economic one. U.S. President Obama has referred to it as an “exceptional” country. But a recent Chinese commentary asked if the U.S. is now a part of the problem, or a part of the solution. It is a valid question.
For example, the U.S. has no monopoly on global brainpower. In fact, the report admits that it is losing that edge. All countries have the right to develop indigenous talent, explore new opportunities in business, science and elsewhere. They also have the right to enjoy this right without it being considered as a potential threat to anyone else, especially a country that is bent on thwarting that threat.
The document will also help readers establish immediate linkages between the U.S. policy agenda as crafted in 2009 and many present-day global developments, such as the efforts to destabilise Ukraine, the resumed intervention in Iraq, the conflicts in the South China Sea, the rise of Japanese militarism, the cementing of Australia’s role as the U.S. deputy sheriff in the Asia-Pacific, the push to expand the Trans-Pacific Partnership economic agreements, and much more.
The report should lead to extensive soul-searching among the expatriate U.S. community worldwide, especially those who are opposed to U.S. government policies. Such individuals will see this report as an exoneration of their views. But in the light of recent developments, exercising their democratic freedoms to voice their opposition may see them being categorised as a “threat” and placed under surveillance by their own government. So much for “freedom and democracy.”
The document also shows how the U.S. government is slowly falling on its own sword. It tries to take account of threats to its national security but fails take account of the biggest threat — whistleblowers of conscience such as Edward Snowden who have put all these documents into the public domain specifically in order to thwart the U.S. government from pursuing its path of unilateral wrongdoing.
This omission means that the U.S. government has no clue how to deal with these whistleblowers, except by threats and intimidation. A country where whistleblowers were once hailed for their critical role in bringing down lying Presidents and ending futile, unsustainable wars (which were also based on lying to the U.S. public) is now trying to silence and incarcerate whistleblowers for holding the administration accountable for lies and deception. Again, so much for “freedom and democracy.”
Another major area of omission, and a potentially greater threat to U.S. national security, is also internal – the army of aerospace and defence contractors who are generously funded by U.S. tax money and are becoming powers unto themselves. Are these companies a part of the problem, or a part of the solution? To what extent are rogue elements amongst them creating and fomenting global problems in order to buttress their corporate bottom-lines? What oversight and check-and-balance mechanism do they operate under? Can the U.S. government rein them in?
The U.S. government has placed itself in a dangerous zero-sum-game situation based on the false assumption that it can remain Top Dog forever. As history shows that no empire lasts forever, the battle to maintain this supremacy via dominating, non-democratic means is setting the stage for a multiplicity of conflicts that will create immense problems globally. Neither can the U.S. extricate itself easily from this dicey scenario without sacrificing its entire credibility on the global stage.
Former U.S. CIA analyst William Blum, writing in his famous book “Rogue State”, said: “The pursuit of the American dream is becoming the rest of the world’s nightmare.” The latest Snowden leak proves that comment 100% true. The U.S. government must be held accountable by all those for whom it is creating problems. That is a global right. As the QICR review says that U.S. businesspeople, academics, students, researchers and others are all to be involved in the effort, it is only a matter of time before more whistleblowers of conscience emerge and expose them. This is already happening as U.S. internet and telecommunication giants begin to fear the looming backlash over compromising of privacy rights.
As I wrote several times in a column that was gagged by the Bangkok Post, the so-called “newspaper you can trust” – Unjust rulers always fall. Always. The only question is: Will they exit gracefully, or take everyone down with them?



Liked this article? Share it!